Consider this scenario: You are gearing up for your holiday shopping and receive an email titled “CYBER MONDAY DEAL: 70% OFF ALL PCs”. You click on the link that enticingly sits next to the words “Click here to learn more.” Your curiosity quickly turns to fear as the URL forwards to a site that declares “WINDOWS HAS DETECTED SPYWARE ON THIS COMPUTER. CALL THIS NUMBER IMMEDIATELY FOR SUPPORT”. You call the number on the screen and agree to pay the voice on the other end a fee to fix the problem because they claim to be a Windows Support Specialist. Once you provide your payment details, you realize that the person on the phone is not Microsoft employee but a bad actor who just took advantage of you for believing that the warning was real.
This is just one of many common phishing tactics that criminals leverage to exploit shoppers during the holiday season. And to make matters worse, these instances are on the rise. According to Cybersecurity company Zscaler, phishing attacks surged by 58.2% in 2023 compared to the prior year.
With trust being an essential factor in successful phishing campaigns, we continue to see domain names that mimic popular brands being used in many attacks. Since it isn’t necessary for a domain name to resolve to a website for it to be used as an email address, understanding the nuances and trends in this threat vector is key to mitigating risk.
The Latest Phishing Trends
GCD recently conducted a study of about 4,000 registered phishing domains from the “phishing. database” repository, one of the largest and most reputable databases of malicious URLs. We sought to determine common trends among these abusive names, such as average length, TLD type, DNS records, and more. This blog provides an overview of the study results and offers tips for domain decision-makers to make it more difficult for bad actors to exploit brands, whether you are looking to protect your current portfolio or prevent scammers from utilizing domains you don’t own.
Focus on Monitoring Legacy Extensions and Risky TLDs
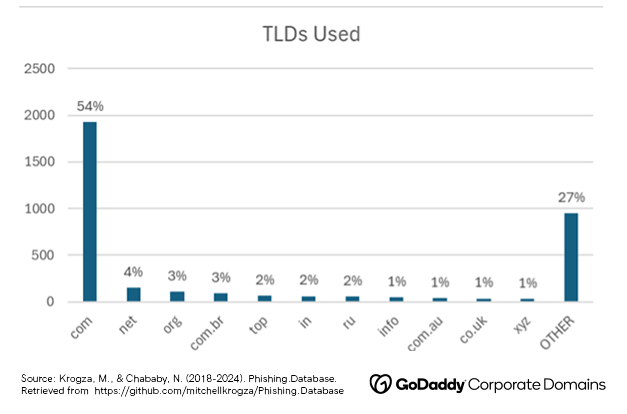
Among the domains in the dataset, legacy TLDs (top-level domains like .com, .net, and .org) were the most common. Hackers often send emails from domains that are perceived as being the most trustworthy to increase the likelihood that a recipient will fall victim to a scam. The .com TLD alone accounted for more than half (54%) of the domains in the study, followed by .net (4%) and .org (3%).
The most common ngTLD (top-level domains like .online, .site, .tech, etc.) used among the phishing names is “.top”, whose registry was recently issued a public breach notice by ICANN for failure to act on reports of DNS abuse. Another interesting finding is that India’s country code (.in) was one of the most common country-code top-level domains (ccTLDs) found in the dataset. India ranked third globally for phishing attacks in 2023, with 79 million total attempts. Domain decision-makers should prioritize acquiring and monitoring defensive registrations in the most popular legacy extensions: high-risk gTLDs, and in ccTLDs, for countries where their brands are well known. For example, if a company does not own its key brands in .top, we recommend securing those.
Keep an Eye on Combination and Typo Domains
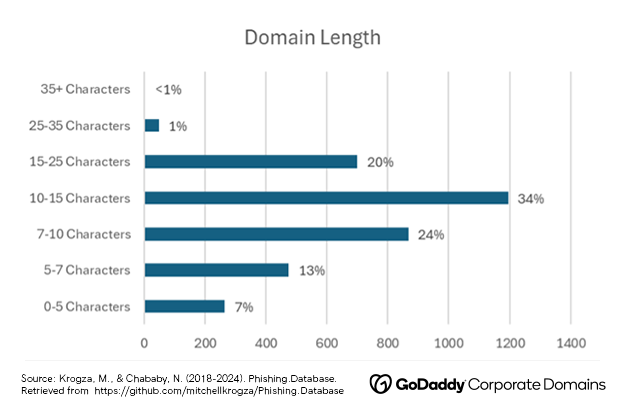
The average length among the domains in GCD’s analysis is about 12 characters. The average length among the world’s most popular 100 brands is around 8 characters, with most company names containing 5-10 letters.
What does that mean for you? The average character count of phishing keywords is slightly longer compared to popular company names. This suggests that phishers may target domains that mimic legitimate brands and add an extra keyword, plural, or typo. This makes it easier for recipients to overlook subtle differences, increasing the likelihood of falling victim to phishing attempts.
Some common examples include “www[Brand].com” (this type of domain takes advantage of customers that mistakenly omit the first period between the www and a company’s main website), “[Brand]Careers.com” (for campaigns targeted at job seekers), and “[Brand]Auth.com” (for employee-targeted phishing campaigns that mimic authenticator tools). The slightly longer nature of malicious keywords in the dataset indicates that brand combinations and typos may be a popular option for perpetrators of phishing campaigns.
The use of combination and typo keywords in phishing campaigns highlights the growing importance for domain decision-makers to proactively protect their brands. Companies should consider using third-party domain monitoring (a Brandsight tracker feature) and professional portfolio consulting services to reduce the risk of a brand getting targeted by bad actors. Domain monitoring helps businesses track the registration and usage of risky domains, alerting them when a DNS change is made that could result in infringement. GCD offers consulting engagements that provide a customized approach to a company’s domain strategy, offering brands a clearer understanding of which infringing domains to look out for.
A tool that can reduce the risk of exact match (such as “example.com”) and homoglyph domain registrations (such as “éxample.com” or “exàmple.com”) is domain blocking. With GlobalBlock, the latest blocking tool, brands can prevent anyone from registering domains that match a given trademark across over 600 extensions, with plans to expand to 800 by 2025.
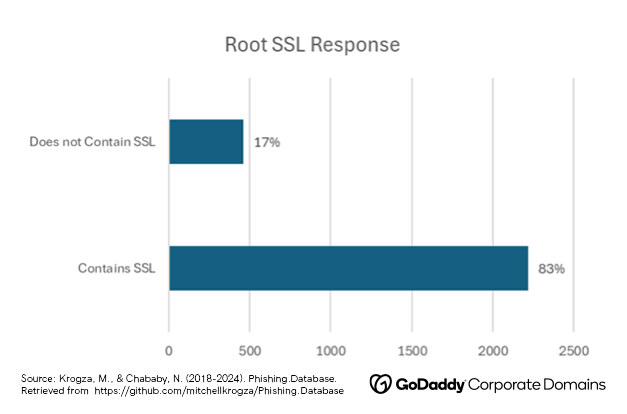
Be Aware: Most Phishing Domains Have SSL Certificates
SSL certificates are digital certificates that offer authentication for websites and allow an encrypted connection between the site and the user’s browser. GCD noticed that most of the phishing domains in the study have this protocol enabled on both the root and WWW. Since most modern browsers mark non-HTTPS domains as “not secure”, bad actors enable SSL certs to make their domains seem more legitimate to victims and email providers. Additionally, obtaining these certs has become easier and more affordable, even free in many cases, with experts estimating a 15x increase in SSL adoption over the past decade.
While it was previously a common belief that most phishing domains lacked SSL certificates, this is no longer the case, and domain decision-makers should be aware of this change when searching for possible infringing domains. It is another example of bad actors evolving and getting smarter. Advanced monitoring tools that continually assess how domains are being used may be helpful for brands to address this issue and decipher which SSL-containing domains are malicious.
Enable DMARC to Counter Bad Actors
While most phishing campaigns involve culprits registering domains themselves, some attacks originate from cybercriminals hijacking a domain that is already owned by a third party. This makes it crucial for domain decision-makers to implement robust security measures that reduce the likelihood of a successful campaign. Implementing DMARC is one of the ways domain decision-makers can make it more difficult for hackers to successfully use their domains for phishing scams.
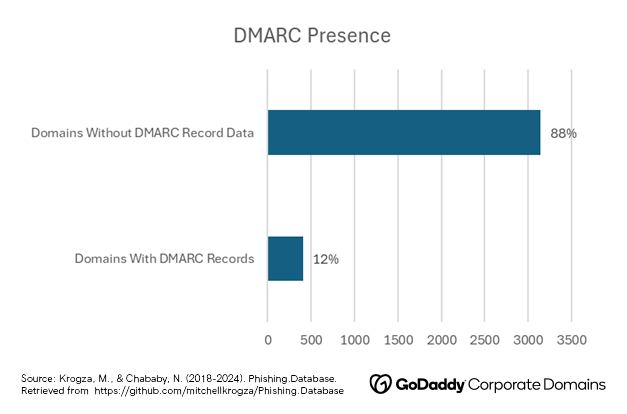
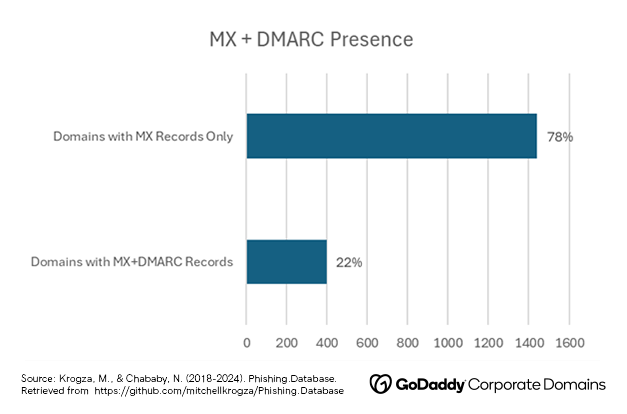
DMARC is a mail authentication protocol that can protect recipients and senders from spam, phishing, and other fraudulent email activities by giving the domain owner the power to choose how their emails should be authenticated. Among the domains in GCD’s study that can send emails, only 22% contain DMARC Records. Without DMARC, it is easier for attackers to impersonate a domain, thereby increasing the likelihood of a successful phishing attempt. This may indicate that bad actors target domains that do not have this record enabled, highlighting the importance that brands configure DMARC for all of their names.
Use SPF Records to Enhance Email Security
SPF records identify which mail servers are allowed to send emails on behalf of a domain. These records help prevent phishing attacks by allowing mail servers to confirm that inbound emails come from a trusted source. A significant percentage (55%) of the domains that GCD studied do not include this framework. This indicates that domains without SPF may be more vulnerable to getting captured for phishing purposes. It is a good practice for domain managers to implement this protocol to enhance domain security and reduce the likelihood of being targeted for hijacking.
Conclusion
The holiday season is a prime opportunity for bad actors to deploy phishing campaigns that mimic well-known brands. Domain decision-makers should focus on a few things to make it harder for cybercriminals to target their company:
- Acquire exact match and high priority typos in legacy extensions (such as .com, .net, etc.) and commonly abused ngTLDs (such as .top and .in), so that cybercriminals cannot register them.
- Consider utilizing domain monitoring tools, consulting services, and GlobalBlock to track vulnerabilities and mitigate the risk of a bad actor registering exact match keywords, homoglyph variants, and combination domains.
- Expand your domain monitoring prioritization to account for bad actors’ use of SSLs. Domain data services, such as GCD’s Brandsight Tracker, are a great option here.
- Implement email authentication protocols (such as DMARC and SPF records) on your own names to better protect them from being compromised.
Taking these steps can reduce the likelihood that employees, customers, and suppliers will fall victim to phishing attacks and can help companies protect their valuable intellectual property from cyber criminals.